Rule Libraries
Rule Libraries are collection of methods that have been grouped together and stored in IdentityIQ as a Rule Object.
To Reference a Rule Library :
To Test a Rule Library using a Task :
Save and Execute
Different Types of Tasks in IIQ :
- Perform Maintenance
- Important for all certification types
- Certification phase Changes : Must run after certifier clicks “Sign Off” to mark certification completed and move it to next phase
- Scan for certification remediations : Manages remediation checking during Revocation period
- Finish Certifications
- Prune Requests : like prune task results, prune batch requests
- Process background workflows.
- Perform Identity Request Maintenance
- To validate the identity requests in a "Verifying" state to determine that they are in fact "Complete".
- To delete old identity requests that are no longer needed, for this can specify the number of days to allow things to be "Verifying" before they get marked "Failed" b/c they can't be verified, and can specify the number of days to keep old, completed/failed Identity Requests. Both of these are settings in the task definition.
- Identity Cube Refresh Task and various options:
- updates identity attributes from the identity account attributes
- run against all identities ( by default )
- update role assignments/detections
- promote entitlements to a certifiable state
- check for policy violations
- run after the aggregation process when cube data needs recalculation
- mark manager status for each identity
- Prune Identity Task :
- Account Aggregation Task :
- The process by which IdentityIQ creates and updates Identity Cubes with account, attribute and entitlement data accessed through configured Applications.
- Account Aggregation is very similar to reconciliation within an identity management solution. Tasks are utilized to perform account aggregation.
- Account Group Aggregation Task :
Multi Object Concept / Multi group Concept :
Till version 6.3 only 2 object types were there :
- Account
- Group -------------->> are entitlements in Identity IQ
But with 6.4 onwards the multi object types introduced as and all these except account are known as access :
- Account
- Profile --- access ( entitlement )
- Privileges --- access ( entitlement )
- Group --- access ( entitlement )
When you do the aggregation of an access of the target system into Identity IQ these accesses will come into Entitlement Catalog and can be considered as entitlements in Identity IQ
Entitlement ------ Access of the target system which can be assigned to the end user. That means all access of target system should come into identityiq in the form of an entitlement, and it should be populated in entitlement catalog.
To bring all entitlements / access from target system , the job which is run is called account group aggregation.
For Example : JDBC Application --- taking department attribute as access
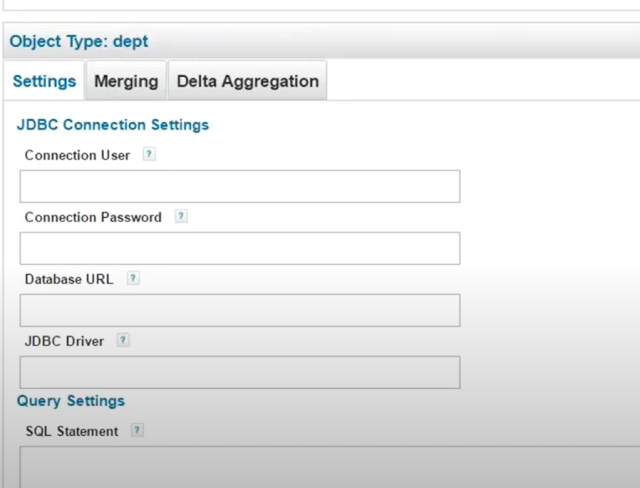
Add Object Type :
New Object type dept created :
Preview
Create Task -- Account group aggregation
Executed Task --- Account group aggregation
Verify in Entitlement Catalog
Now to provide a relationship between department attribute and object type dept
select in drop down of department attribute as dept
So now the department is an access so make it as entitlement and managed
Now Run First Account group aggregation and after Account group aggregation run next account aggregation of the application.
Now verifying department name in identity ware house for 1 identity
Note: suppose if want to make any attribute to come in Entitlement Catalog simply make it managed and then run account aggregation with the check box checked for Promote Managed Attribute
And this is the reason why Entitlements are enerally marked as Managed to get the entry in Entitlement Catalog
verify in Entitlement Catalog