Integration of Active Directory with SailPoint IIQ The AD connector uses IQService to talk to AD.
IQService, also referred to as the Integration Service or Server Host, is a native Windows service that enables IdentityIQ to participate in a Windows environment and access information only available through Windows APIs.
The following sources typically require IQService:
- Active Directory
- Azure Active Directory
- IBM Lotus Domino
- SharePoint
Integration of Active Directory with SailPoint IIQ
The AD connector uses IQService to talk to AD.
IQService, also referred to as the Integration Service or Server Host, is a native Windows service that enables IdentityIQ to participate in a Windows environment and access information only available through Windows APIs.
IQService is a windows based agent written in .net languages. It leverages APIs provided in Windows environments to provide provisioning services for IdentityIQ's Java based technologies. IQService is installed as a service running on a Windows OS based host. By default it listens on TCP port 5050 for requests from IdentityIQ systems.
Before to use the provisioning feature of the connector, the IQService must be installed and registered on any Windows system with any of the supported Operating System i.e. Active Directory.
Prerequisite:
- For user provisioning through IQService, required that the administrator has the appropriate rights on the Active Directory.
- The Domain Controller should be accessible from the IQService host computer
To install and register the IQService, perform the following:
1. Create a directory in which you want to download the service. For example, c:\iqservice.
1. Create a directory in which you want to download the service. For example, c:\iqservice.
2. Extract the IQService.zip archive from the IIQHOME\WEB-INF\bin\win directory of the IdentityIQ.
3. Run the following command to install a Windows service named IQService.
3. Run the following command to install a Windows service named IQService.
- exe –i
- Check the Service status in Windows machine:
- Goto –>run–> services.msc.
- Look for IQservice
Check the connectivity between Active Directory and the Host machine.
- Install Apache studio or any LDAP browser to connect with Active
- Provide connection Details and check Network Parameter.
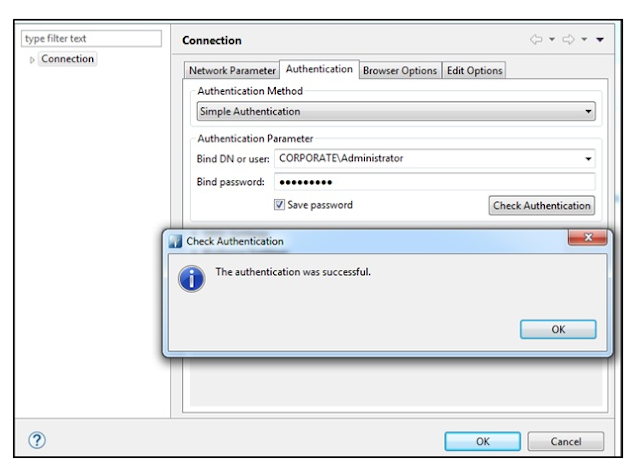
Provide Credentials for Active Directory User having administrator Rights. Below Screen shows a successful connection and Authentication with Active Directory from Host machine.
Post successful Authentication Log into Active Directory lookout for Directory Structure as this would require in configuring the application in next step.
Log into Sail point (IIQ) Application
Application Configuration
- Go to –> Application àApplication Definition
- Add new application
- Provide the Name of the application
- Owner details in the case of approval workflow are there to validate and approve the request before the creation of the
- Revoker Detail to authorize the Account revokes operation.
- Provide Details of IQservice Installed on Active Directory Windows machine.
- Default port for IQ service is 5050
Domain configuration Include details of Service /Admin account for communication between the host machine and Active Directory i.e Username, ServerIP, Password, Domain address.
Configuration of Account:
This configuration is used for Account Aggregation. This process will fetch account details from input DN of active directory and link them with Identities present in IIQ.
Configuration of Group:
This configuration is used for Account Group Aggregation.This process will fetch all groups/entitlement details from given search DN of active directory. These groups will be available in entitlement Catalogue as well post Group Account Aggregation run.
After all configuration just clicks on test connection to ensure all configuration are correct.
- Go to Configuration –> Schema
- Click on Discover Schema –> this will pop up all attribute from Active directory.
In Active Directory Integration, we would require User Accounts as well as groups information.So same step we have to follow to pop group attribute from active Directory.
At the bottom of attribute page, Click on Preview tab to check the data structure before running any aggregation in the application.
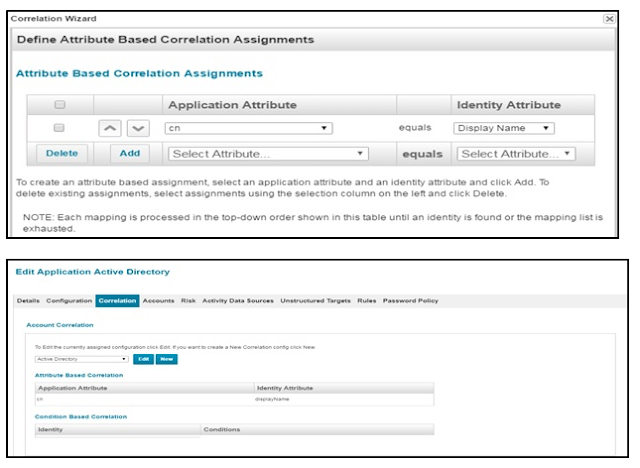
Setting up Account Correlation attribute .This is require to link account based on unique attribute.
In IIQ there are two type of Correlation:
- Account Correlation
- Manager Correlation
Both Account and Manager Correlation can be Attribute based or Condition based.
Attribute Based correlation: It will use the application Account attribute to find the identities based on the attribute value of the IIQ Application.
For Example Application Account attribute “cn” can be used to link/correlate Identity attribute “Username”.
Condition Based Attribute: In some application like “Unix” when there is no identifying attribute exist which can be used to correlate the account with identities. For the root account on Unix typically does not have any identifying attributes that can help when trying to correlate it to an existing identity
Condition based Attribute correlation can be help for correlation Service and Administrator accounts might be handled using condition based correlation
Go to Correlation –> Account correlation
Click on New and Name the Account correlation
Manager Correlation:
Manager correlation is required to link manager based on the attribute defined in target application and attribute in IIQ application.
Now Application configuration is done and Application is ready for Account aggregation.
Aggregation:
There are two type of Aggregation mainly execute in IIQ Sail point i.e.
- Account aggregation
- Account group aggregation
Account aggregation tasks scan applications configured to work with IdentityIQ, discover users and entitlements on those applications, and, optionally, correlate those users and entitlements with roles
Account group aggregation tasks are used to scan applications and aggregate account groups and application object attributes. These are then used for group certification (either permissions or membership) or for displaying of group information in identity certifications
Configure Account aggregation
- Go to Setup à Task
- New Task
- Select Account Aggregation
- Configure it as per below screen.
- Select Application to scan: Select Active Directory Application from the drop
- At the bottom Click in Save and execute
Configure Account Group aggregation
- Go to Setup –> Task
- New Task
- Select Account Group Aggregation
- Configure it as per below screen.
- Select Application to scan: Select Active Directory Application from the drop
- At the bottom Click in Save and execute
To check the status of this account Group aggregation.
- Go to –> Setup
- Task –>Task results —> Active Directory Account Group Aggregation.
Check User details in Identity :
To cross check the user Account check this user in Active Directory:
NOTE :: few things need to highlight : Sailpoint , IQservice , AD Forest this whole package ( AD Forest + IQService ) installed in windows server.
IQService has port default port 5050 listens and suppose both have same Windows server IP Address : 192.168.15.100 because both are on same windows server.
in AD Forest we will give some root example like dc=example,dc=com while installation and here dc=example,dc=com( called domain name) and dc=example called forest name or also you can say NETBIOS name
so what happens when you do provisioning from sailpoint to AD then it goes like sailpoint to IQService then AD but when you do Reconciliation ( means Aggregation ) then it is directly from AD to Sailpoint no need IQService for reconciliation or aggregation.
By default any LDAP product runs on 389 port so AD Forest port and IQservice default port is 5050
Now prerequisite of AD integration is done and now starts with AD integration with Sailpoint. Now for integration any application we just create a virtual copy of the application in sailpoint for example here for AD application we will will create a virtual copy in sailpoint and will provide all the details like on which port it listens what is forest name what is GCS global catalog server what is domain name etc.
GCS so global catalog server is windows server so ipaddress of windows server where the iqservice and ADDS are installed and forest name is as an dc=example and domain name is dc=example,dc=com and what is master user detail as wmservice\administrator is a master user which is created on windows server 2012 r2 and iqservice port is 5050 and AD port is 389.
so what are steps :
1) Configure basic application details means your application instance is ready.
2) Configure the Schema means to create Road through whic Application Atrributes walk into the sailpoint and that Road is called as Schema.
3) Create Correlation b/w user and account means b/w sailpoint and AD -- now all users will not come all Accounts will not come only filtered accounts will come means there should be some condition based on which we will filter because everything will not come from AD to Sailpoint so some filtered accounts will come and that is done by the Correlation. for example bring those users which satisfy condition like x = y now in sailpoint there is an authoritative application attribute username navneet.kumar and in AD there is an attribute samAccountName navneet.kumar so username = samAccountName condition meets so this user will bring into sailpoint using correlation and we will restrict other user means we will not bring those accounts into sailpoint from AD whose users are not present in sailpoint. But if you will not correlate everything will come into Sailpoint from AD.
4) Create Account Aggregation Task for accounts and if required create Group Aggregation Task for groups- Now all the things done we picked what are the accounts will come and now we will take vehicle to bring those accounts means with the help of Aggregation Task.So Aggregation Task is a vehicle.using this vehicle you bring all the data into sailpoint.