Managing IdentityIQ
User Access
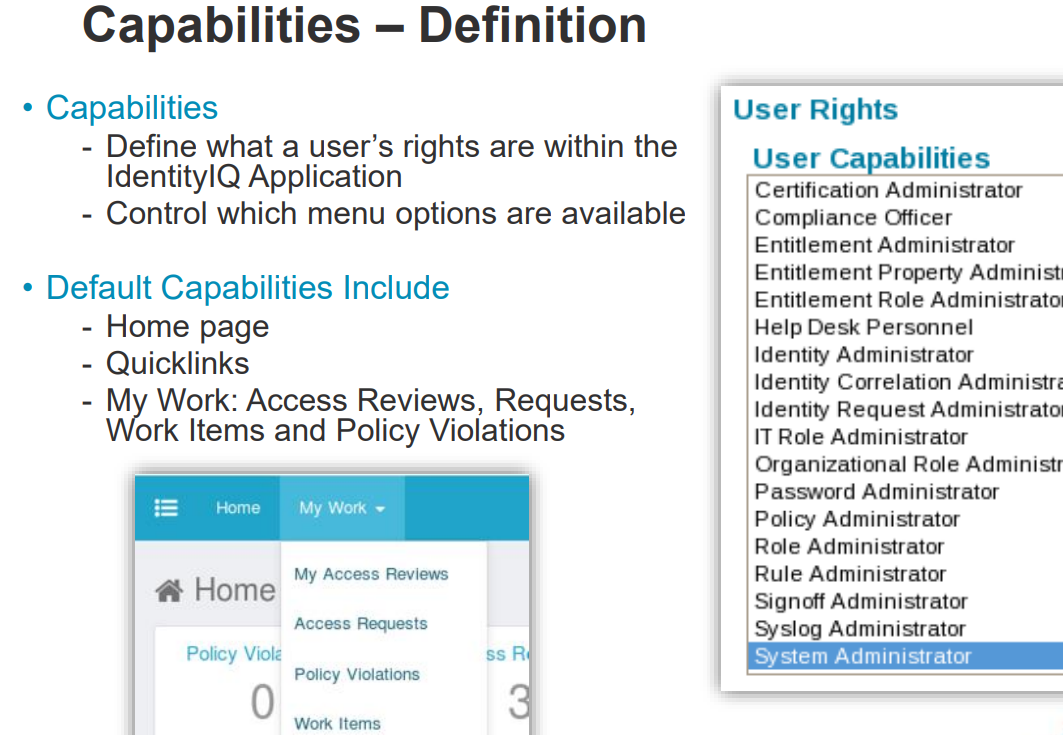
Capabilities/Scoping and Workgroups control identities access
to IdentityIQ
IdentityIQ’s scoping functionality provides an additional level of control over the segments of data on which a user can perform these tasks. With scopes, customers can subdivide their data into logical groups and grant access based on those subdivisions. For example, perhaps a Compliance Officer for the Americas region should only be able to see details about the identities within the Americas region. This can be managed by defining scopes based on identities’ "region" attribute values ("region" being an extended attribute defined for the installation).
When scoping is enabled, both scope and capabilities are used to determine each user’s access within the system. A user must still have the appropriate capabilities to be able to view and manage objects. Scoping just limits the objects to which the capabilities are applied.
Scoping 2 Types
- Assigned Scope is the scope in which an object exists, or the scope to which it belongs. Every object in the system will be assigned zero or one scopes. An object’s assigned scope determines who can view and manage the object. By default, an object that does not have an assigned scope is available to everyone. This behavior can be inverted through a system configuration property; with this inverted behavior, only system administrators can view objects that do not have an assigned scope.
- Authorized Scope is a scope over which an identity has access. Only identities who control (authorized for) that scope can see/manage objects. Every identity in the system can be authorized to zero or more scopes. An identity’s authorized scopes determine the set of objects they can see in the system while the capabilities assigned to the identity determine what they can do with those objects. Identities can only access objects whose assigned scope matches (or is a child scope of) one of the Identity’s authorized scopes. Authorized scope is also sometimes called “controlled scope”.