- SAILPOINT IdentityIQ integrates provisioning and compliance features into a single solution. Thus this IDM product is able to address all the needs related to Identity and Access Management such as Access Certifications, Policy Enforcement, Account Provisioning, and User Life-Cycle Management.
Sailpoint Architecture
Organizations should be able to use their identity solution to enable clear and comprehensive controls on access to data and applications, allow for proper access requests, and timely provisioning of access rights, with the number of new vendors, staff, and other people come on board.
The Architecture of SailPoint IdentityIQ consists of four major components as follows
1) Compliance Manager
2) Lifecycle Manager
3) Governance platform
4) User provisioning
Advantages of Automated Identity Lifecycle Management
1) Minimizing the risk
Users have access to the right tools for the right purposes due to Lifecycle Manager. using IdentityIQ Compliance Manager to conduct routine certification campaigns, and access checks, and provide a complete audit trail giving a better understanding of who has access to whom and when and where the access was given.
2) Minimizing the IT Helpdesk Load and Costs
End users should handle their own authorization requests, which relieves IT organizations of any of their workload. Business users can request full self-service access through IdentityIQ,
3) Improve Efficiencies
automatic provisioning controls the business processes of authorizing, changing, and revoking access. Changes in user access can be provisioned
4) Automate Policy Management
IdentityIQ Lifecycle Manager in combination with IdentityIQ Compliance Manager to identify separation of duties (SoD) policies and other policy concepts that provide controls
- Concept of Identity Cubes and Identity Attributes:
- SailPoint IdentityIQ represents users by Identity Cubes.
- “Cubes” are built through a discovery process from authoritative sources i.e. by bringing in user account data from Authoritative Applications and are refreshed dynamically or by running a Identity Refresh Task
- Example of Identity attributes are Name,Email,department etc.
- Application Account Exists inside Identity Cube
- Identity Attributes
- Entitlements/Roles
- Risk Score
- Policy Violations
- User Rights ( Capabilities/Scoping )
Hibernate Files - IdentityIQ allows you to customize extended and searchable attributes by editing various .hbm.xml files such as :
IdentityExtended.hbm.xmlLinkExtended.hbm.xml
Identity Attribute: Non Searchable
- do not set source and target mapping of same application-attribute pair, it creates circular references where value continuously changes with every attribute sync
Provision All Accounts: Incase if user has more than 1 account in your Target application, then SailPoint doesn’t know in which account it needs to update. So you select that checkbox, so that it will update in all the accounts under same target application for that user.
- Transformation Rule: As the name indicates, if you need to transform the value.
For example, if Job title is Senior Analyst but your target system would like to have the value as Sr. Analyst, then you need to write some script to change the value accordingly.
- Native Change Detection :
- Delta Aggregation
- For directories connectors (for e.g. LDAP, AD), there could be a change log or last modification timestamp that is used to figure out what has changed,
- For database a special table needs to be created to keep track of added, updated and removed records and a trigger to fill this table. The JDBC connector will check the table for changes (like a change log in LDAP) and then get the relevant records one by one.
- A ManagedAttribute is essentially an entry within the entitlement catalog.
- If the attribute is "managed" and you select 'promote managed attribute' in aggregation, then this will look at each account it is processing and determine whether the entitlement(s) on that account already exist in IdentityIQ's database or not, and if it does not exist, it will create the entitlement in the entitlement catalog. So, if you set the attribute as "managed" it can be promoted to entitlement catalog.
- In schema definition, there is a property that can be set on every attribute that indicates 'managed'. Another property 'entitlement' is what tags it as an entitlement. If it checks entitlement, managed is automatically checked.
- The main difference is that managed entitlements would show up in places like certifications/etc., whereas managed attributes (not marked entitlement) won't.
- "multi-valued" check on a schema attribute make that attribute a "managed attribute" or not, the answer is "No".
- For Multi-valued, attributes flagged as multi-valued are stored as a list. Even objects that have a single value for a multi-value attribute are stored as a single-item list. Multi-valued attributes are used for queries throughout the IdentityIQ. Before multi-valued attributes are available for use in searches, they must be mapped on the Edit Account Attribute page.
- For Managed, specify attributes to promoted to a first-class object in the IdentityIQ database so that they can be associated with other objects with that value, for example a description or an owner. Any attribute can become managed: department, location, title, but the most common attribute to be managed is the one holding group memberships. Managed attributes can be viewed and managed from the Entitlement Catalog page.
- Orphan Accounts : Every account always becomes part of an identity. So if a newly read account cannot be "correlated " to an existing identity , a new identity is formulated or can say is created. If the application from which the account is coming is not marked as " authoritative " the account or identity is considered " unauthoritative " or " orphaned " so when run aggregation process on authoritative application , accounts those are not correlated successfully goes into " Orphan Accounts ".
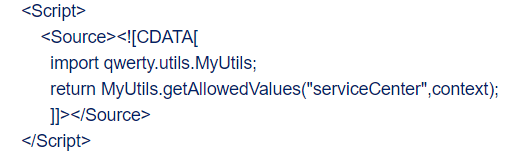
- CDATA :
- QUICKLINK :
Custom QuickLinks are most typically used to launch workflows, link directly to other pages in the IdentityIQ user interface, and launch external web links.
These custom QuickLinks can do any of these things:
- Launch a custom workflow
- Launch an external web link
- Directly link to other pages in the IdentityIQ UI
Note : To restrict quick-link need to configure DynamicScopes as :

- DynamicScopes :

Integrating SailPoint AI Services - to integrate AI Services with IdentityIQ i.e. implementation of SailPoint AI Services in IdentityIQ by importing the AI Services init-ai.xml file into IdentityIQ:
browse to the following directory:
identityiq_home\WEB-INF\config
whereidentityiq_homeis the directory in which you extracted theidentityiq.warfile during the IdentityIQ installation procedure.Select the
init-ai.xmlfile and click Import.
- Plugins must be enabled in IdentityIQ for AI Services to be installed. Ensure that
plugins.enabled=truein theidentityiq_home/WEB-INF/classes/iiq.propertiesfile of your installation. - Integrating AI Services with IdentityIQ helps your organization determine who should have access to what. AI Services uses peer group analysis and identity attributes to recommend access to your users, and to help certifiers decide when user access should be approved or denied. AI Services can also identify user access patterns to determine potential roles that accurately align with what users actually do in an organization
- Decision Recommendations
- Access Request Recommendations
- Automatic Approvals
IdentityIQ Plugins
The SailPoint Plugin Framework is an extension framework model for IdentityIQ. It enables third parties to develop rich application and service-level enhancements to the core SailPoint platform. It enables plugins to extend the standard user interface, deliver custom REST endpoints, and to deliver custom background services.
A plugin can be a simple REST service or a full page application on top of IdentityIQ. A plugin can include one or all of the following:
A client side front end
REST web services
ServiceDefinition, PolicyDefinitions, and TaskDefinition implementations
Java classes available for scripting
Custom plugin configuration
Database tables
During your initial installation, IdentityIQ is set up to work with plugins. A separate plugin table, identityiqPlugin, is created as part of the database schema creation scripts and the plugins.runSqlScripts, plugins.importObjects, and plugins.enabled properties are set to true in the iiq.properties file.
Working with Plugins in IdentityIQ
The plugin feature must be enabled in IdentityIQ and you must have the proper access, such as System Administrator or Plugin Administrator capabilities, before this page can be displayed.
The Installed Plugins page displays and enables you to manage your plugins from within IdentityIQ. Open the page by selecting Plugins from the list under the gear icon.
From the Installed Plugins page you can install, uninstall, enable, disable, and configure your plugins.
Install – click New and either drag and drop a zip file onto the page, or navigate to the directory containing the plugins.
Enable/Disable – click the power button icon to enable or disable plugins. You will be asked to confirm your decision.
Uninstall – click the X icon to uninstall a plugin.
IdentityIQ stores the .zip archive file of the Plugin in the IdentityIQ database in a data LONGBLOB in the spt_file_bucket table. The data in the spt_file_bucket table is referenced ID to an entry in the spt_persisted_file table.
Plugins are loaded from this .zip file after installation or after an application server restart. The .zip file is extracted, and all important files are cached for later use. There are several accessor methods to reference the cached files, but they can also be referenced by the url prefix /identityiq/plugin/pluginName followed by the path found in the build structure. Compiled java classes are loaded and cached from the .zip archive using the PluginClassLoader class.